Last Updated on October 9, 2023 by KnownSense
In this page, we’re going to look at all the technologies at a high level that can be used to secure your microservices architecture, and as you’re already aware, our microservices architecture is made up of many moving parts that communicate with each other using the network, and therefore we should adopt some rules for the security of Microservices and to secure our network communication.
HTTPS Everywhere
By using HTTPS everywhere using technologies like SSL and TLS, we can ensure that all our communication is encrypted when it’s between our components.
Network Security
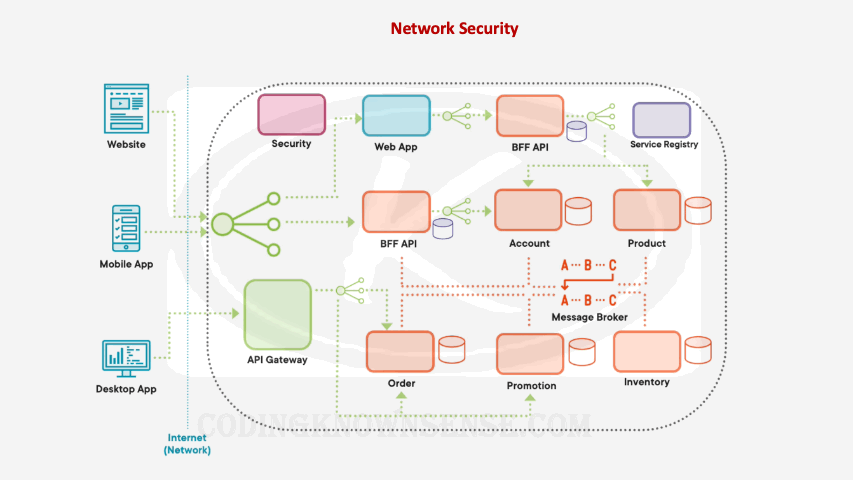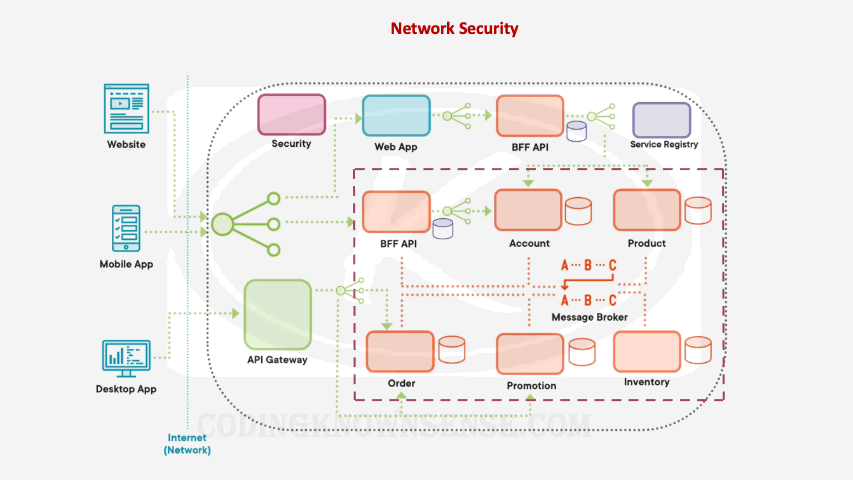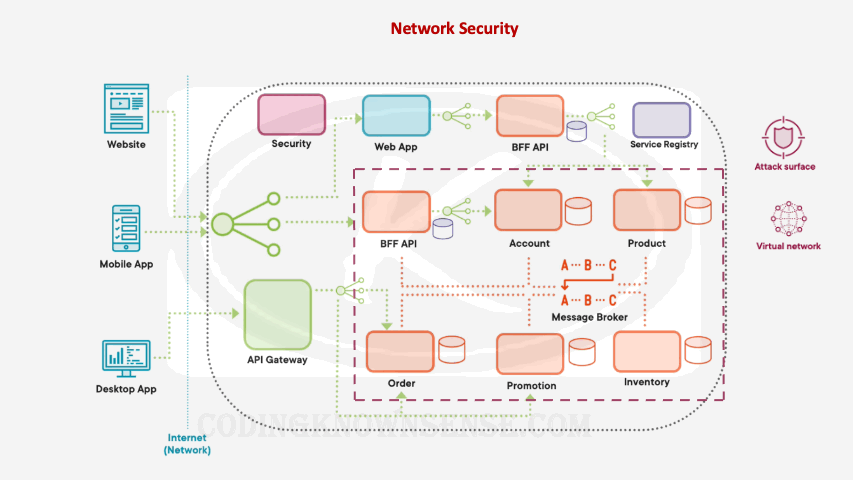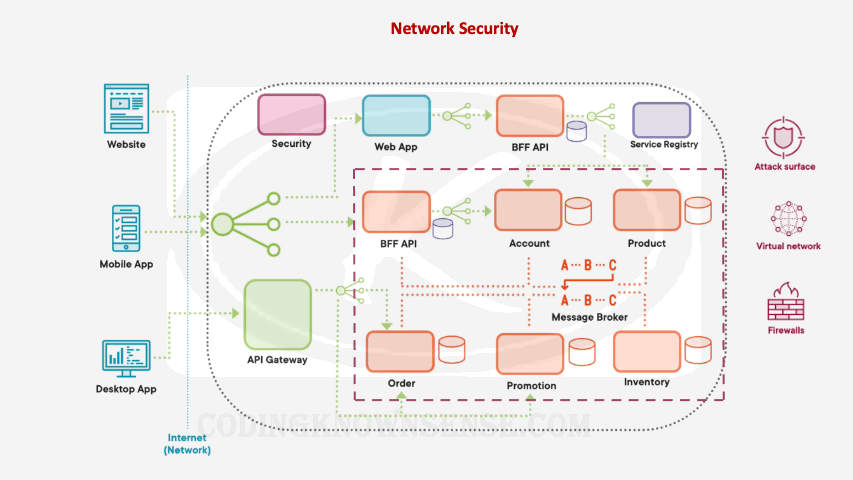
The other thing we should try and do is reduce the attack surface within our microservices architecture and that basically means minimizing what exposed on the internet. So for example, if you have a set of microservices and databases where nothing talks to them directly, place these microservices and databases into their own virtual network or into their own private network. Then in addition to this, we can use components like firewalls to control exactly what client applications can talk to the public part of our network and the private part of our network. We can even have our front‑facing components like the API gateway and the back in for front end API, include extra security measures like, for example, core rate limiting to avoid things like DDoS attacks where we stopped taking calls when we’re receiving too many malicious successive calls from the same location. One thing I’ve learned about both security and technology is that both are moving targets, and therefore, sometimes it’s worth getting a dedicated specialist team to do penetration testing on your microservices architecture. Basically, a third‑party organization that specializes in penetration could be used periodically to ensure everything is secure on your microservices architecture.
Centralized Security: Authentication and Authorisation

Another thing we need to think about in terms of application level security is instead of having all the security built into an application like you would do with a large application. For our microservices architecture, we should have a central security component and this central security component should be used to provide things like authentication to identify your users in a consistent and reliable manner across all your microservices architecture. The same security component can also be used to provide authorization services where you can state exactly what client applications can access what backend services and also authorization in the sense what can our users do within our applications and what can they do within our microservices in terms of accessing data and functionality. The good news is there are now established standards which help provide these type of functionalities and technologies standards like OAuth2, OpenID Connect, and Token Exchange. In a nutshell, they basically work by passing around an identity token which includes all the user authentication information for your users and an access token which includes all the authorization information that all your microservices and backend systems need. The other key thing is do not try and reinvent the wheel, there is already off‑the‑shelf products available that can provide this kind of centralized security mechanism following these standards, things like Azure AD, Okta, Ping Identity, and identity server, and many more. There are centralist components which provide this functionality already.
Securing Message Broker/Service Bus
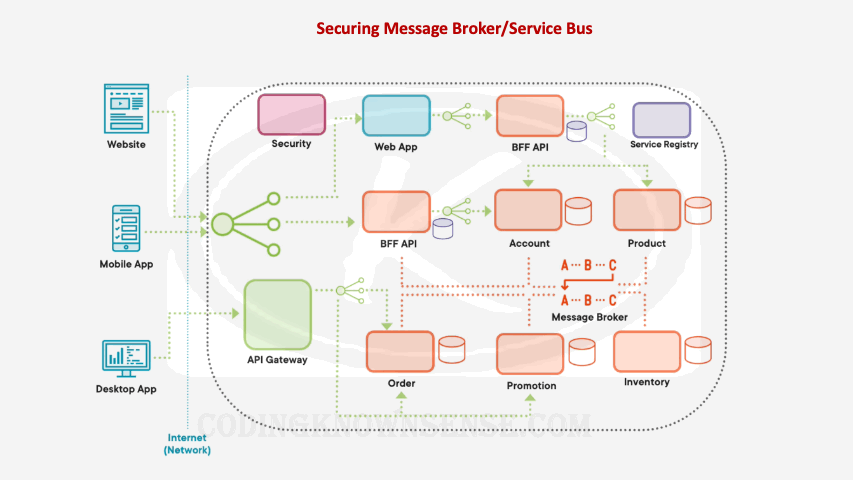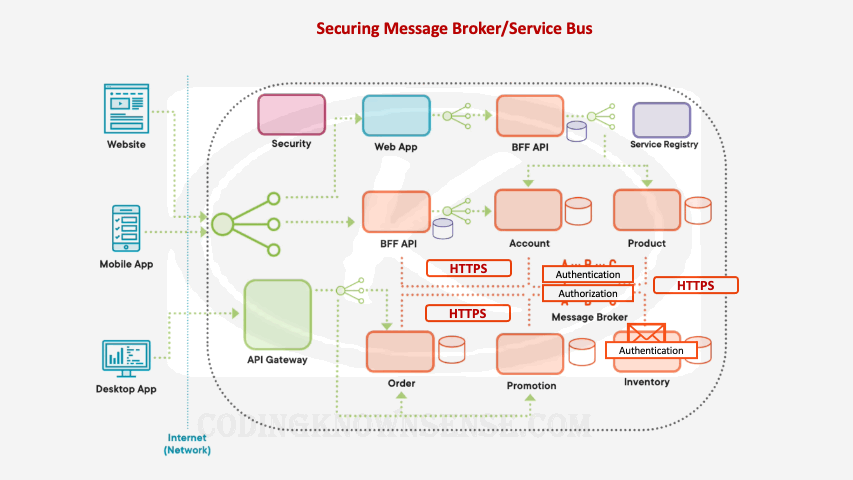
When it comes to security, we’re not only worried about the security of our microservices, but also the security of other components within our microservices architecture, things like the message broker, things like our central logging system, things like our central monitoring system, are we using authentication and authorization and https to communicate to these components
Conclusion
The page outlines key strategies for securing a microservices architecture, including the widespread adoption of HTTPS encryption, the isolation of microservices and databases within private networks, and the use of firewalls and rate limiting to reduce vulnerabilities. It emphasizes centralized security components for consistent user authentication and authorization, leveraging standards like OAuth2 and OpenID Connect, and recommends off-the-shelf solutions like Azure AD and Okta for implementation. Additionally, the page underscores the importance of securing auxiliary components, such as message brokers and monitoring systems, with authentication, authorization, and HTTPS to enhance overall architecture security.